How to Configure SSL (HTTPS) for Exploratory Collaboration Server
This document explains how you can set up SSL for your Exploratory Collaboration Server.
It has 3 parts.
- Place SSL Certificate Files
- Configure SSL for Collaboration Server
- Configure SSL for Scheduler
Place SSL Certificate Files
Place your SSL certificate file and private key file under the “ssl” directory, which is under the “exploratory” directory created by expanding the downloaded compressed file for Exploratory Collaboration Server.
If you don’t find “ssl” directory under “exploratory” directory, create it and place the SSL certificate file and private key file in it.
In the explanations below, we assume that the SSL certificate file is named fullchain.pem, and the private key file is named privkey.pem.
Configure SSL for Collaboration Server
Update docker-compose.yml
Open the “docker-compose.yml” file under the “exploratory” directory and make the following changes under the “nginx” section.
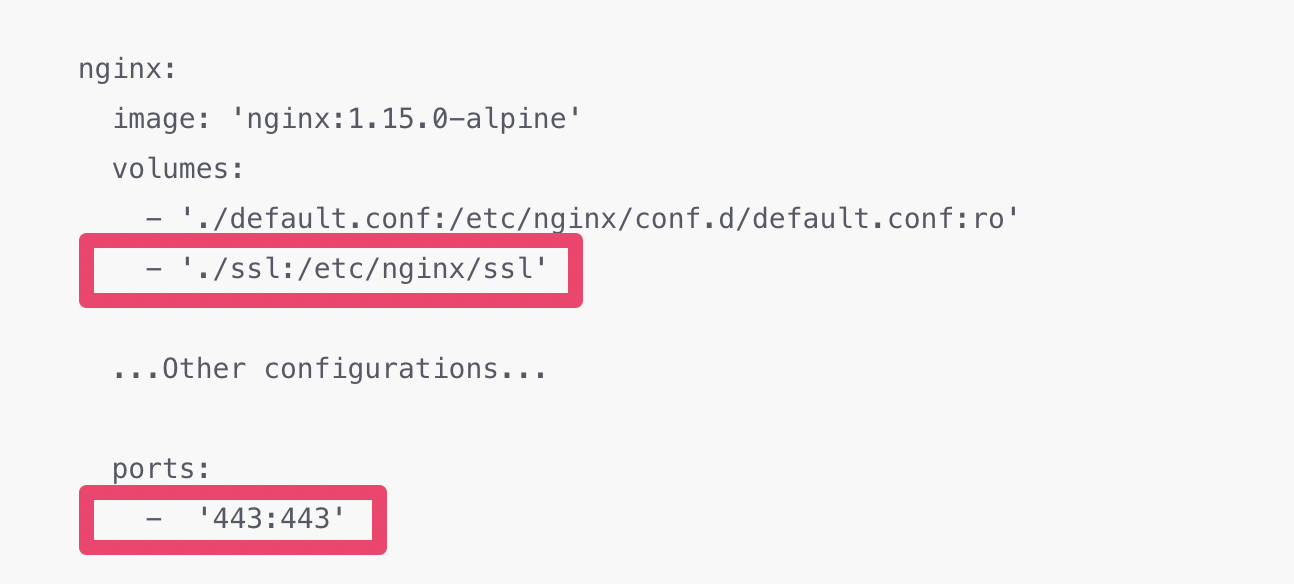
- Add
- './ssl:/etc/nginx/ssl'under the “volumes” section. - Replace the original
- '8080:80'with- '443:443'. This is to make use of the port number 443, the default port number for SSL (HTTPS) connection.
Original configuration in docker-compose.yml:
nginx:
image: 'nginx:1.15.0-alpine'
volumes:
- './default.conf:/etc/nginx/conf.d/default.conf:ro'
...Other configurations...
ports:
- '8080:80'The updated configuration in docker-compose.yml:
Update default.conf
Open the “default.conf” file, which is the configuration file for the nginx web server, under the “exploratory” directory. Make the following changes.
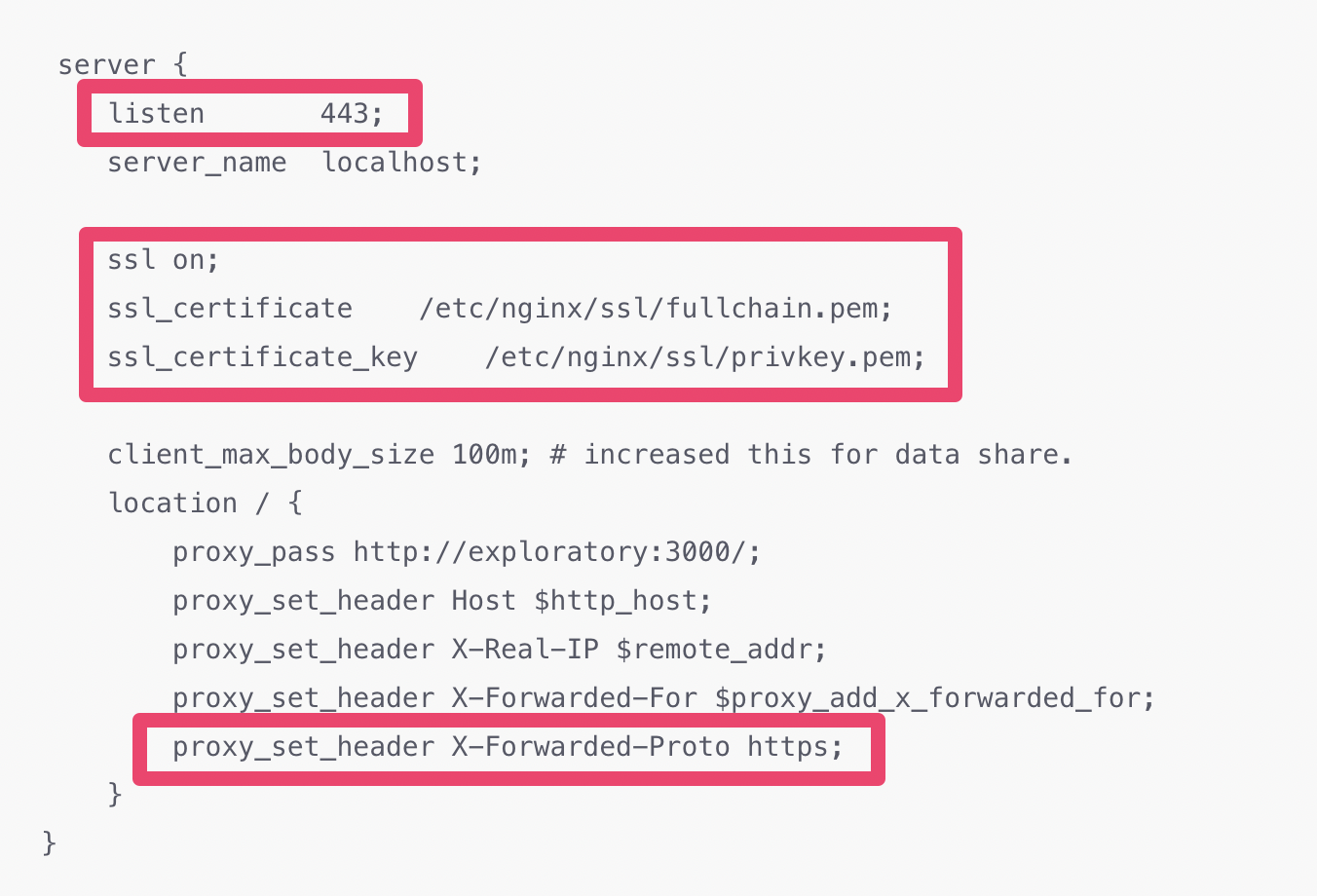
- To make use of the port number 443, which is the default port number for SSL connection (HTTPS protocol), replace the original
listen 80line withlisten 443. To enable SSL, add
ssl on;. Also, specify the file names for SSL certificate and private key like the following example. Please replace the file names in the configurationfullchain.pem, andprivkey.pemwith the actual file names you are using.ssl on; ssl_certificate /etc/nginx/ssl/fullchain.pem; ssl_certificate_key /etc/nginx/ssl/privkey.pem;To use “https” as the protocol for the URLs to be generated in the server (e.g. URL of created Dashboards), instead of “http”, modify the line
proxy_set_header X-Forwarded-Proto httpto beproxy_set_header X-Forwarded-Proto https.
Original configuration in the default.conf:
server {
listen 80;
server_name localhost;
client_max_body_size 100m; # increased this for data share.
location / {
proxy_pass http://exploratory:3000/;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto http;
}
}
Updated configuration in the default.conf:
Configure SSL for Scheduler
Agendash, which is the admin UI server for the scheduled jobs, can be accessed at port number 3001, and by default it uses HTTP without SSL. To set up SSL (HTTPS) on port 3001, please make following configuration changes.
Update docker-compose.yml file
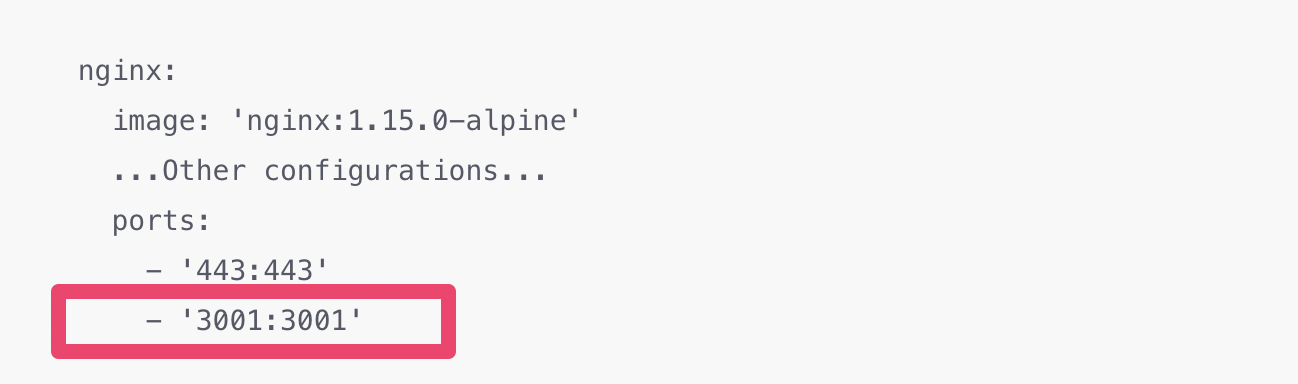
In the docker-compose.yml file under the “exploratory” directory, add a line - '3001:3001' under ports section under nginx section. This is so that nginx web server, which does the encryption/decryption for the SSL connection, can receive requests coming to the port 443.
The original configuration in docker-compose.yml:
nginx:
image: 'nginx:1.15.0-alpine'
...Other configurations...
ports:
- '443:443'
The updadate configuration in docker-compose.yml:
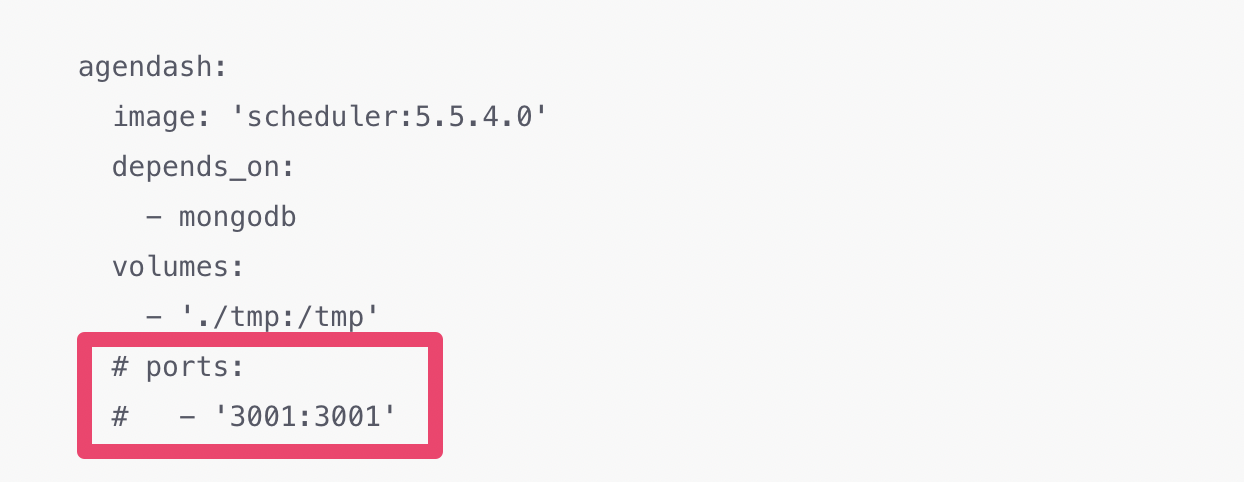
Also, delete or comment-out the lines ports: and - '3001:3001' in the agendash section. This is so that agendash does not receive the requests coming to the port 3001 directly, now that nginx web server is the one to recieve them.
Original configuration in docker-compose.yml:
agendash:
image: 'scheduler:5.5.4.0'
depends_on:
- mongodb
volumes:
- './tmp:/tmp'
ports:
- '3001:3001'
Updated configuration in docker-compose.yml (With commented-out lines):
Update default.conf file
Add the following configuration at the end of the default.conf under “exploratory” directory. Please replace the filenames fullchain.pem, and privkey.pem with the actual filenames of your SSL certificate file and private key file.
This configuration is for nginx web server to receive the requests at port 3001, decrypt them with SSL, and forward them to the Agendash.
server {
listen 3001;
server_name localhost;
ssl on;
ssl_certificate /etc/nginx/ssl/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/privkey.pem;
location / {
proxy_pass http://agendash:3001/;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
}
}Original:
server {
listen 443;
server_name localhost;
ssl on;
ssl_certificate /etc/nginx/ssl/fullchain.pem;
ssl_certificate_key /etc/nginx/ssl/privkey.pem;
client_max_body_size 100m; # increased this for data share.
location / {
proxy_pass http://exploratory:3000/;
proxy_set_header Host $http_host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto https;
}
}
After the update:
